
Amazon has confirmed and fixed a vulnerability in its Photos app for Android, which has been downloaded over 50 million times on the Google Play Store.
Amazon Photos is an image and video storage application that enables users to seamlessly share their snaps with up to five family members, offering powerful management and organization features.
The flaw, discovered by researchers at Checkmarx, lies in a misconfiguration of an app component, resulting in its manifest file being externally accessible without authentication.
Exploiting this bug could have enabled a malicious app installed on the same device to snatch Amazon access tokens used for Amazon APIs authentication.
These APIs might contain sensitive personal information like full name, email, and physical address, while others like the Amazon Drive API hold user files.
Exploiting the flaw
The vulnerable component is “com.amazon.gallery.thor.app.activity.ThorViewActivity”, which, when launched, triggers an HTTP request that contains a header with the user’s token.
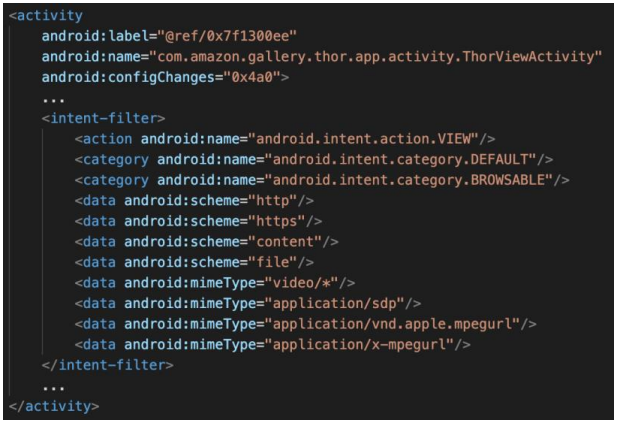
Checkmarx researchers found that an external app could easily launch the vulnerable activity and trigger the request at will, sending the token to an actor-controlled server.
.png)
The analysts explored various exploitation scenarios with the acquired token, such as performing file actions on the victim’s Amazon Drive cloud storage, erasing history so that deleted data is irrecoverable, and more.
“With all these options available for an attacker, a ransomware scenario was easy to come up with as a likely attack vector,” details Checkmarx
“A malicious actor would simply need to read, encrypt, and re-write the customer’s files while erasing their history.”
The same token might be used by other Amazon APIs, like Prime Video, Alexa, Kindle, etc., so the exploitation potential could be far-reaching.
Disclosure and fix
Checkmarx reported the issue to Amazon on November 7, 2021, and the internet giant confirmed the reception the next day, classifying it as a high-severity vulnerability.
On December 18, 2021, Amazon informed Checkmarx that they had resolved the issues via a security update deployed into production. However, users of the app were never informed of the potential exposure.
We have reached out to Amazon to ask if they noticed any signs of exploitation of the vulnerability and whether there have been reports of unauthorized Amazon API access during that period, and a spokesperson has provided us with the following comment:
At Amazon, privacy and security are foundational to how we design and deliver devices, features, and experiences. We appreciate the work of independent security researchers who help bring potential issues to our attention.
We released a fix for this issue soon after it was brought to our attention. We have no evidence that sensitive customer information was exposed as a result of this issue.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now